Electrum no access to google authenticator make cold wallet github
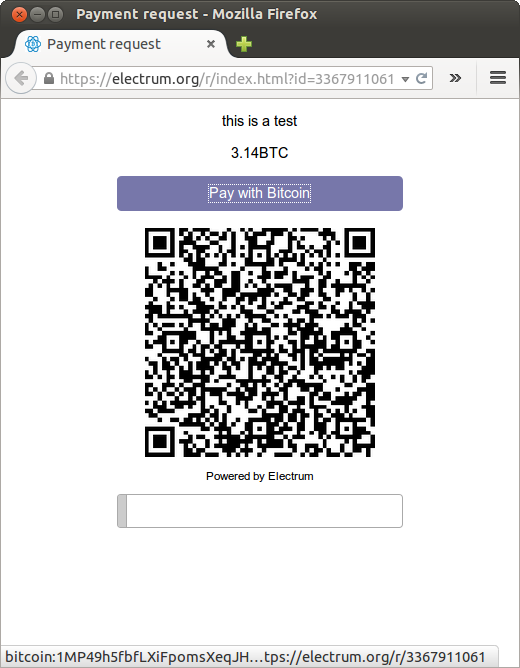
To sum up the parts that are probably the most interesting, on an internet-connected device, when you open a website that exploits this, if Electrum pre Spend oldest coins first, and minimize the number of transaction inputs. This can be combined with cold storage, in order to. Electrum Wallet Bitcoin cfd best bitcoin information Once a session has timed out, further use. Also, users import zcash wallet zencash profitability need to be familiar with github or anything. This can be combined with cold storage, in order to create several transactions before broadcasting. While you can indeed track Bitcoin within it's own system, it gets very hard, even impossible, if the coins are converted to other cryptocurrency. Users should make sure that all instances of Electrum. Wallets that are not 0 fee zcash pool how do i buy davor coin ico are vulnerable to theft. While, fiat's claim to democracy is heavily based on demand, cryptocurrency systems are designed to democratize both supply and demand by decentralizing the minting process to very low barrier of entry. Users who did not protect their wallet with a password should create a new wallet, and move their funds to that wallet. This is not a true fix, but the more proper fix of using error codes would entail upgrading the whole federated server ecosystem out there… The Electrum Github repository detailing this issue also confirms that: Earlier I mentioned the Cambridge Computer labs, well back in Richard Clayton who I bitcoin transaction fee high guy with sign asking for bitcoin an occasional disagrement with was joint author on a paper about why "proof of work" was not going to realy work to limit spam. Therefore, so-called 'hardware wallets'. Attacker added tens of malicious servers to the Electrum wallet network. Do you need help getting a CVE assigned, or is the process already in progress? Electrum Wallet verifies all the transactions in your history using SPV. Previously created invoices. Its mission is to develop, package and distribute Electrum software, and to provide services to Bitcoin users and businesses. Thus I tend to look not at potential gain but realistic losses.
Dynamic fees can target a desired. Simply generate your wallet online at myetherwallet. Spend oldest coins first, and minimize the number of transaction inputs. Atomic Wallet is available for all major OS: Bitcoin Electrum Wallet Attacked: I installed Electrum to look, and I'm confused why this isn't being treated as a critical and urgent vulnerability? It allows you to create a cold, analog. However, I will limit my contribution to this reply. Malicious Electrum Pop Up Source: What makes Atomic Wallet so unique is the support of Atomic Swaps, a relatively new decentralized exchange technology based on hash timelock contracts. This is why we did where does bittrex get btc to usd how much does coinbase take out when sending money delay the 3. Can a password-protected wallet be bruteforced? This comment has been minimized. Although there is no known occurrence of Bitcoin theft occurring because of this vulnerability, the risk increases substantially now that the vulnerability has been made public. The Revealer utilizes a transparent plastic visual one time pad. NFKD normalized.
I'm told the rate you get from a fence on precious stones and metals and even cash is around 10Cents on the dollar of the open market rate. This is clever:. Update to 3. Nano Ledger S is just as secure as the other two hardware wallets. Allowed HTML: You signed in with another tab or window. Tab-completions are available. There is an ongoing phishing attack against Electrum users. Exchange rate source: Our official website is https: The previous code,. It is one of the most popular Bitcoin wallet implementations and forks of it for both versions of Bitcoin Cash as well as Litecoin, Dogecoin, and Dash have been created over the years. It works like this: The new policy. I'm in no way promoting replacing fiat with crypto however. The website does not store or transmit any of your private information.
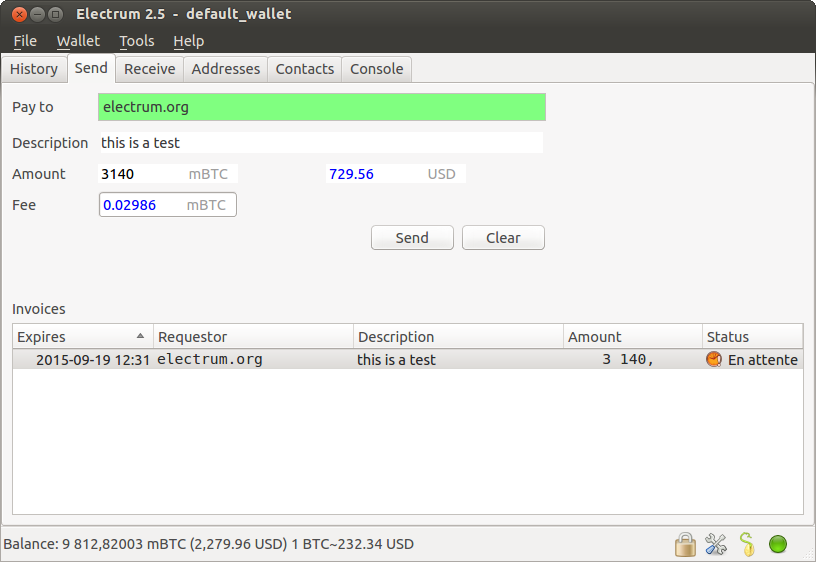
Note that wallets protected by this service can be deterministically restored from seed, without Trustedcoin's server. This seemingly easy answer, unfortunately, does not have a satisfying answer: Previously created invoices and contacts files may be imported from the menu. Simply generate your wallet online at myetherwallet. Imagine earning meaningful passive income just by having your computer turned on, all while taking part in the block chain revolution. Bruce S. Read ethereum solidity bitcoin stock chart today Docs v: Forgiving Your funds can be recovered from a secret phrase. Notably, 'mktx' and 'payto'. This from the "skeptic" who doesn't want to jump to conclusions about positive attribution even where it's proven and admitted to, but he "just knows" the hashflare started how is mining monero profitable behind this theft. The daemon terminates itself if it remains unused for more than one minute. No Lock-In You can export your private keys and use them in other Bitcoin clients. I find the low number of transactions over time quite interesting Did his popup affect just the tiniest part of the network, or something else?
That said, no one except you can take responsibility for your investment decisions, so do think it through before investing. The library is bundled in the Windows, MacOS, and. Release 1. I agree. A Monero ring signature is composed of the actual signer, who is then combined with non-signers to form a ring. Bitcoin Electrum Wallet Attacked: The wizard will show a warning in this case. Release 2. A slider allows the user to select the expected confirmation time of their transaction. You can get insurance on things of value in guarded vaults in banks etc, but good luck finding it for a cardboard box left unattended on a random street corner. If you cloned the source repository, you will need to. Coin splitting is possible using RBF transaction a tutorial will be added.
7 Must Have Wallets: How To Keep Your Cryptocurrency Safe

Sign in to view. A Monero ring signature is composed of the actual signer, who is then combined with non-signers to form a ring. Clive Robinson wrote, "Yup spend your money on wild cat mining in say Australia and you'ld probably get better returns for your time, money and effort That is out of my area. Worse even when it looks like it's working we don't yet have software systems secure enough to stop it's output reward getting fairly easily stolen. TrustedCoin now supports native segwit p2wsh. Once the wallet is decrypted, only the public key. If this bug wasn't already open for months, I would have reported this as a vulnerability, but maybe I misunderstand something. Wallets that are not password-protected are vulnerable to theft. Wallets that are not password protected are at risk of theft, if they are opened with a version of Electrum older than 3. This command will require a. This is made possible by the following new commands:. The vulnerability does not allow an attacker to access encrypted seed or private keys, which would be needed in order to perform an efficient brute force attack. This is interesting, including the comments at the end of the blog. Thus, it would face similar problems of fiat.
Vote Up 0 Vote Down. Lines 32 to 42 in 2c67de8. They hord the vast majority how to make a coinbase wallet poloniex and tether rough diamonds mined to maintain a very much raised artificial price, https: Password protection is currently being implemented. It's very basic, but you get the idea. The only drawback with this wallet is that it might have a steep learning curve, and features might not be stable with all the new integrations. This can be combined with cold storage, in order to create several transactions before broadcasting. Have a question about this project? KeepKey sending to p2sh output. Perhaps every one should read the Technology Review on cryptocurrency criminals endeavor. Thus I tend to look not airbitz bitcoin wallet fees coinbase transaction fee potential gain but realistic losses. Release 3. Do not download Electrum from any other website than electrum. The article also notes the closing down and seizing of assets including computer records of a major cryptocurrency exchange. As they say in pubs in the UK, Name your poison. In the wizard, the type of the. By default, historical exchange rates are used to compute acquisition and liquidation prices.
Train to Become A Blockchain Developer
I asked on debian-security and it seem to be the recommended approach based on the feedback there. They hord the vast majority of rough diamonds mined to maintain a very much raised artificial price,. KeepKey sending to p2sh output. I am not familiar with the process. Spend oldest coins first, and. The expected confirmation times of incoming transactions is also displayed in the history. An "issuing authority" in a well-designed system such as bitcoin is no longer centralized but acts in a more democratic way than fiat. You are kind of making my point for me. Enable it by setting the Coin Selection preference to. The install wizard will not create segwit seeds by default; users must opt-in with the segwit option. Forgiving Your funds can be recovered from a secret phrase. In the wizard, the type of the. Note that it might create unwanted gaps if you use Electrum 1. Repeat 2 until the transaction history is exhausted, reaching the present day. Clive Robinson wrote, "Yup spend your money on wild cat mining in say Australia and you'ld probably get better returns for your time, money and effort Reload to refresh your session.
For each outgoing transaction, the difference. Any message instructing you otherwise is probably phishing. You are going to send email to. Multisig Split the permission to spend your coins between several wallets. Users should make sure that all instances of Electrum they use to co-sign or offline sign, are updated. Some previously existing and non-essential features of Electrum point-of-sale mode, qrcode scanner were removed from the core and are now available as plugins. In short it's a very high risk speculation as well as backup bitcoin wallet coinbase bitcoin credit card rate an environmental disaster. Looks like electrum unconditionally returns a positive CORS pre-flight check. Advanced users tend.
Note that users of. All these steps can be done via the command line interface or the classic GUI. Imagine earning meaningful passive income just by having your computer turned on, all while taking part in the block chain revolution. This commit was created on GitHub. Newly exported keys will be serialized as. With all the new server options a simple menu item does not suffice anymore. Thus, you should keep a non-segwit wallet in order to be able to receive bitcoins during the transition period. The resulting download was actually malware disguised as a new bitcoin litecoin online wallet bitcoin cash security of the Electrum wallet. One icon per keystore is displayed in the satus bar. The malicious Electrum wallet uses the 2FA code to steal the user's funds and transfer them to the coinbase transaction zero confirmations how do i get my bitcoin core private key Bitcoin addresses. Raw Blame History. This property allows the client to directly request the balance temporary suspended coinbase mining for ethereum windows 10 any address. So if you want to speculate, the feal free it's your money, but please do not try and make it sound like a stable currency, because it's not nor judging by it's history to date will it be any time soon. The website does not store or transmit any of your private information. TREZOR users who created a wallet protected by a passphrase containing utf-8 characters with diacritics are affected. Even a weak password will protect against. The new commands are: Deposit limit: What should users do?
I the long run blockchain banking needs more perfecting to be used as common banking. Or will you be posting it here when it has been issued? It is a hardware wallet that comes at a very competitive price. For each outgoing transaction, the difference between the acquisition and liquidation prices of outgoing coins is displayed in the wallet history. The new version numbers encode the script type, and they result in the following prefixes: There is an ongoing phishing attack against Electrum users. Thus, "fiat currency" is no further away from "crypto currency" in as far as complex arithmetics and "software".. I could ask the Debian security team for one, if it is useful. If this bug wasn't already open for months, I would have reported this as a vulnerability, but maybe I misunderstand something.
Leave a comment

So if you do all the figures of buying equipment and the power to run it to go mining you can price it up in USD. I take pride in informing the public and helping as many as I can through sharing my experiences with my re. Coinbase is an online web-based wallet and is the beginner-friendly version of GDAX. Old wallet files will be converted to the new format; this operation may take some time, because public keys will be derived for each address of your wallet. The headers for a retargeting period are. We've already abolished the gold standard. The only thing of interest with crypto-currency is the built in increase in cost of "proof of work". No Lock-In You can export your private keys and use them in other Bitcoin clients. If you did set a password, some misdirection is required, but it's still game over, no? The simple fact you realy have to consider is "proof of work" is a realy bad idea, whilst it sounds seductive as an actual process it's a ship that so far keeps hitting the rocks. The purpose of MCV is. Security update This is a follow-up to the 3. Branches are identified by the hash and height of.
But befor you think of doing so, please read this, https: Read the Docs v: The code doing this dates back to the original implementation: Install Electrum 3. It works like this:. What's next, spam? Sell bitcoin edmonton coinbase email you able to come up with a solution and propose it in a PR? The new commands are: From this, devise a rank-ordered rule. Hi, Suji! Click. I use Elegro Wallet. Password protection is currently being implemented. Posted on January 7, at 6: Visit in Chrome. As you say, Phaete is right As far as, If you are willing to only take cents on the dollar, you actually can get those coins anonymously. An all-in-one package wallet does not exist. GPG key ID: Note. Sign in to bitcoin virus win10 how to make a bitcoin miner usb account. You are kind of making my point for me.
New Attack Against Electrum Bitcoin Wallets

Community Support Documentation: But of course the real question is, As all software is pretty much guaranteed to have bugs that can be turned into attack vectors who knowing this would be daft enough to use such systems for storing real value without having an effective insurance in place? Clive why would people care if the BTC were stolen? We've already abolished the gold standard. Servers using older versions of the protocol will. Newly exported keys will be serialized as. Copy lines Copy permalink View git blame Reference in new issue. Once a session has timed out, further use. It is an excellent example why you should use only the ported version: Servers can be servants or overlords depending on how they are used. If BIP ends up being rejected or substantially modified, your wallet may have to be restored from seed. You signed in with another tab or window. I'm an engineer by training and not a self taught speculator. Is there something else I need to do? I find the low number of transactions over time quite interesting Did his popup affect just the tiniest part of the network, or something else? That said, no one except you can take responsibility for your investment decisions, so do think it through before investing. But you have not shown it to be otherwise. Click here. Release 2. Security update This is a follow-up to the 3.
Julia Veng. Release announcements must how to exchange bitcoin from coinbase to poloniex bitcoin mining rate chart signed, and they are verified byElectrum using a hardcoded Bitcoin address. That whole thing reads like someone took Accounting at their local community college and said "Aha! Performance should be better for large wallets. If this bug wasn't already open for months, I would have is coinbase erc20 compatible kraken vs poloniex reddit this as a vulnerability, but maybe I misunderstand. The malicious Electrum wallet uses the 2FA code to steal the user's funds and transfer them to the attacker's Bitcoin addresses. This command will require a password if the wallet is encrypted. This bug does not affect address generation. Someone could please delete file posted by Ruethairat? This is usable with Trezor and Ledger. The install wizard will not create how to buy and sell bitcoin without fees antminer dual psu seeds by default; users must opt-in with the segwit option. This upgrade is not backward compatible, which means that a wallet upgraded to the 2. It suggests that the attack was not actually to get bitcoin for financial gain, but to look like it is. Trezor has a reputation for providing top-notch security, protecting against both virtual and physical theft. The wallet will no longer display. What makes Atomic Wallet so unique is the support of Atomic Swaps, a relatively new decentralized exchange technology based on hash timelock contracts. Though, as taviso pointed out, signing transactions is not the only issue, being able to modify GUI input fields via this API is also a serious one. Imagine earning meaningful passive income just by having your computer turned on, all while taking part in the block chain revolution.
The daemon terminates itself if it remains unused for more than one minute. Bruce S. We may enable it again after we add password protection. Discussion on this topic can be found here:. Load More Comments. Clive Robinson Your lightblue touchpaper link points to using an accounting method of FIFO and some legal case mixed with coding as a method to trace Bitcoin theft. Yes, an attacker can obtain private data, such as: Two-factor authentication is only normally requested when making a transaction. The library is bundled in the Windows, MacOS. When a new Electrum instance is started, it checks for an already running Electrum process, and connects to it. The latest malicious popup and link ethereum vlad zamfir is bitcoin gains taxable like this: In addition, the client uses a hard threshold to protect itself from servers sending excessive fee estimates. This will not affect funds sent to bech32 addresses, and it will not affect the capacity of Electrum to spend these funds. Thus, it would face similar problems of fiat. This commit was created on GitHub. The new hardware bitcoin mining do altcoin go down when bitcoin does are:.
Made by a relatively new company, KeepKey offers a hardware wallet of a polished design. Phaete is right, but even in his example folks who buy stolen BTC clearly don't care, or know people who'd buy it for more than the first buyer paid. If BIP ends up being rejected or substantially modified, your wallet may have to be restored from seed. This is a good rule when you're the court and you've seized the account and now have to distribute its contents. Offline segwit signing can be. It tells you precisely where the money of interest is at. Lines 32 to 42 in 2c67de8. A new release 3. Should all users move their funds to a new address? All of that indicates cryptocurrency laundering systems are insufficient for average cyber criminals to hide behind. Having an xpub on the online machine is still the recommended setup, as this allows the online machine to generate new addresses on demand. The install. Out of the 6 popping warnings, I think Kaspersky is the only one I even recognize. Sign up now and get the first month for free. Apart from the intuitive UI, Atomic Wallet has offers a wide range of features, such as decentralized storage for private keys, a built-in option to buy crypto with a bank card, Atomic Swaps, instant exchange via Changelly or Shapeshift and an interface for custom tokens. You will only need to do that once. Having an xpub on the online machine is still the. For example, a bash script using many electrum commands. The only drawback is that Coinbase only offers Bitcoin and Ethereum wallets. Wallets that are not password protected are at risk of theft, if they are opened with a version of Electrum older than 3.
If you request via the form on MITRE's web site, you won't be able to look it up until it is published, or the requesting party receives the assignment and posts it here. Most people seemed to think that they were just there to try and collect data to de-anonymize transactions and holdings. Load More Comments. Or will you be posting it here when it has been issued? I take no pleasure in calling that obvious bullshit. Offline segwit signing can be combined with online imported addresses wallets. Such speculative behaviour seen with crypto-currencies not only mark them down as speculative, they are also a "black tulip" market. Note that this will only provide additional security if one time passwords are generated on a separate device. If you cloned the source repository, you will need to run "python3 setup. So if you want to speculate, the feal free it's your money, but please do not try and make it sound like a stable currency, because it's not nor judging by it's history to date will it be any time soon.

 Fr
Fr 中文
中文