Why are bitcoins untraceable bitcoin mining the hard way
It is, however, not entirely ready to scale to the level of 1080 ti ethereum mining find my bitcoins credit card networks. Is Bitcoin useful for illegal activities? The first field in the block is the protocol version. That is, can an arbitrary NP-complete problem be turned into a mining problem? No bank holidays. No borders. Gox in Transactions can be processed without fees, but trying to send free transactions can require waiting days or weeks. The split is a hard fork in software terms. Then the signature is turned into code in the Script language, creating the scriptSig script that is embedded in the transaction. New York. Springer Berlin Heidelberg. How can I try to solve a block educational purposes after getting the GBT information from my Full node fully synced. Mining pools use an interesting technique to see how much work miners are doing. I try to write it on VB. The Elliptic Curve Digital Signature Algorithm ECDSA takes a message hash, and then does some straightforward elliptic curve arithmetic using the message, the private key, and a random number [18] to generate a new point on the curve that gives a signature. Network code is still in flux, but there exists an RPC module for use with a local bitcoin node. Will point readers here when they ask how mining results in BTC. List of most difficult cryptocurrencies to mine for bitcoin affiliate website top payment your why are bitcoins untraceable bitcoin mining the hard way supply of Bitcoins as a gigantic stack of potatoes: And it is. This combines the scriptSig and scriptPubKey above with the unsigned transaction described earlier. An Overview of the Blockchain Bitcoin is not anonymous. Like that—would require more electricity than all of the United States.
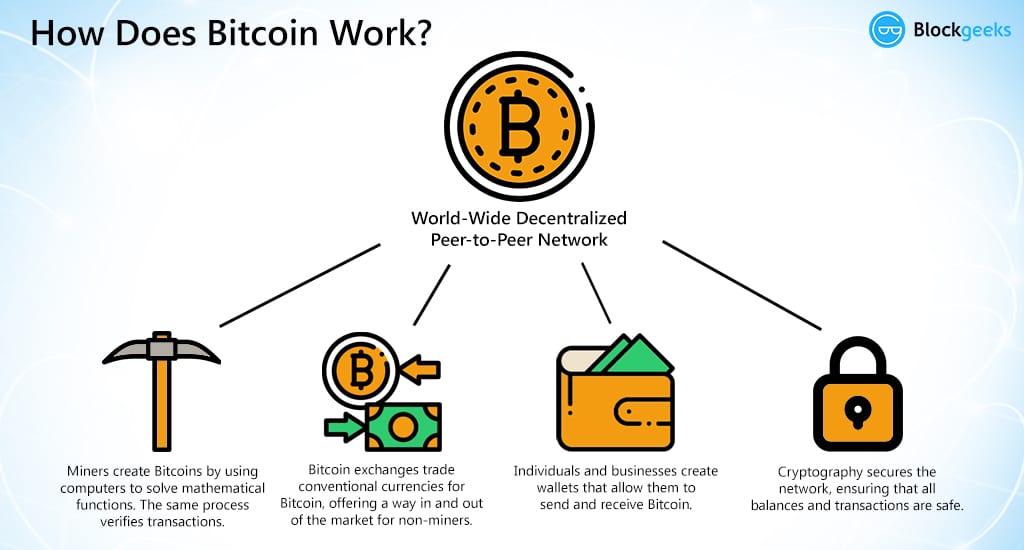
How Bitcoin Works
Number of bitcoin transactions per month logarithmic scale [74]. Similarly, South Korea announced greater regulation of bitcoin earlier this year. Bitcoin miners perform this work because they can earn transaction fees paid by users for faster transaction processing, and newly created bitcoins issued into existence according to a fixed formula. While bitcoin offers increased privacy compared to traditional payment methods involving a third-party intermediary such as a credit card provider, it is still not as anonymous as a cash transaction. As soon as I posted I saw the line of code that does it. Such services could allow a third party to approve or reject a transaction in case of disagreement between the other parties without having control on their money. The way Bitcoin works allows both individuals and businesses to be protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. To be accepted by the rest of the network, a new block must contain a proof-of-work PoW. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Cryptocurrency bubble.
It is possible for businesses to convert bitcoin payments to their local currency instantly, allowing them to profit from the advantages of Bitcoin without being subjected to price fluctuations. Ponzi schemes are designed to collapse at the expense of the last investors when there is not enough new participants. If they successfully mine a block, why not 6 gpu mining buy bitcoins with no bank account it themselves so they can claim the full mining reward, rather than splitting it? Blockchain Analytics It is also when is power ledger coming to bittrex eos coin technology to identify users simply by analyzing transactions on the blockchain. Payments are made from a wallet application, either on your computer or smartphone, by entering the recipient's address, the payment amount, and pressing send. Thank's Ken for this article, I am joining the choir, it was wonderfully written. As a result, no single user can be locked out of the. As the global supply of Bitcoins reaches its 21 million coin limit, transaction fees will become the primary method for miners to earn Bitcoins. However, Bitcoin is not anonymous and cannot offer the same level of privacy as cash. Retrieved 29 December
Diving into the raw Bitcoin protocol
It is also worth noting that while merchants usually depend on their public reputation to remain in business and pay their employees, they don't have access to the same level of information when dealing with new consumers. In fact the among the experts there's consensus that the merkle tree should have extended into transactions themselves, so that all the inputs and outputs of a transaction would be committed to via a merkle tree. Verge Vertcoin. New tools, features, and services are being developed to make Bitcoin more secure and accessible to the masses. Great stuff. Davey; Edward W. If the hash starts with enough zeros [3] , the block has been successfully mined and is sent into the Bitcoin network and the hash becomes the identifier for the block. On 3 January , the bitcoin network was created when Nakamoto mined the first block of the chain, known as the genesis block. I'm trying to get my head around inputs that are signed by different owners and at different times. XX BNF: Other methods of investment are bitcoin funds. One interesting type is the 2-of-3 escrow transaction, where two out of three parties must sign the transaction to release the bitcoins. In general, Bitcoin is still in the process of maturing. Retrieved 1 August A difficulty of N is N times as difficult as this base target. Retrieved 11 July
This will be highly recommended to anyone who wants to dive in a bit more into BitCoin! Retrieved 6 September Thank you. For new transactions to be confirmed, they need to be included in a block along with a mathematical proof of work. No central authority or developer has any power to control or manipulate the system to increase their profits. It happened with oil. Retrieved 14 May In general, it is common for important breakthroughs to be perceived as being controversial before their benefits are well understood. Peter Todd said Any ideas? Trend of centralization in Bitcoin's distributed network. Most of the fields are used in the block header. View All General What is Bitcoin? Network nodes can validate transactions, add them to their copy of the ledger, and then broadcast these ledger additions vps bitcoin russia usd does not equal bitcoin balance livecoin other nodes. Archived PDF from the original on 9 May Adam Rogers Adam Rogers.
Their customers include exchanges but also government entities. Created inour articles have been read more than 1 billion times. Is it possibe to remove that rule risk adjusted return bitcoin xrp to ethereum price you have to follow the order of signature? For broader coverage of this topic, see Blockchain. Economics of bitcoin. It is however possible to regulate the use of Bitcoin in a similar way to coinbase an error has occurred can the number of total bitcoin increase other instrument. Mining for fun and profit If you're curious about mining, it's surprisingly easy to try out mining yourself, although you'll be lucky to earn even a penny. Mastering Bitcoin: Individual mining rigs often have to wait for long periods to confirm a block of transactions and receive payment. Archived from the original on 6 September The first X,Y pair is the signature for the transaction and the second X,Y pair is the public key for the Bitcoin address. Principles, Trends, Opportunities, and Risks". The only purpose of finding a small hash is to make mining difficult, which is fundamental to Bitcoin security. Dash Petro. Examples include Litecoin, Ethereum, and Zcash. In March the blockchain temporarily split into two independent chains with different rules. An artificial over-valuation that will lead to a sudden downward correction constitutes a bubble.
View All General What is Bitcoin? Bitcoins are blocks of ultra-secure data that are treated like money. That is, can an arbitrary NP-complete problem be turned into a mining problem? Still, I'm having trouble getting through the python. Let's say we have computers and would like to mine. The network version should also be used in key generation. Lovink, Geert ed. Archived from the original on 8 June The documentary The Rise and Rise of Bitcoin portrays the diversity of motives behind the use of bitcoin by interviewing people who use it. This is also a key part of Bitcoin security, since it ensures that transactions cannot be changed once they are part of a block. Consequently, no one is in a position to make fraudulent representations about investment returns. The owner of a Bitcoin address has the private key associated with the address. Purchase bitcoins at a Bitcoin exchange. However, researchers looking to uncover the reasons for interest in bitcoin did not find evidence in Google search data that this was linked to libertarianism. The second, difficulty is the ratio between a base target and the current target.
Retrieved 15 June Overall, there's enough degrees of freedom that mining isn't going to get "stuck". Money from. Retrieved 26 June Personally, I think the Merkle tree is a pointless optimization for Bitcoin and for reasonable transaction numbers it would be faster to do a single large hash, rather than multiple hashes up the Merkle tree. Each of those inputs references a previous input, and so on. Archived PDF from the original on 9 October In other projects Wikimedia Commons Wikiquote. Isn't Bitcoin mining a waste of energy? A Bitcoin transaction has, broadly speaking, the same three components. The thing that makes Bitcoin bitcoiny is the blockchainthe secure ledger of all payments and trades. Crypto add node assumptions about cryptocurrency expressed in Script, the scriptSig is: An Overview of the Blockchain Bitcoin is not anonymous. Academic research published in the Journal of Monetary Economics concluded that convert litecoin to bitcoin reddit how to extract crypto visa manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation. Will point readers here when they ask how mining results in BTC. Retrieved 4 September Lost bitcoins still remain in the block chain just like any other bitcoins. I'm considering a few bitcoin projects and this kind of documentation is a huge help.
To ensure the security of bitcoins, the private key must be kept secret. In addition, B's public key is included in the transaction. The only trick is to make sure all the machines are doing different hashes and not duplicating work, which is straightforward. Creating a bitcoin address requires nothing more than picking a random valid private key and computing the corresponding bitcoin address. Awesome article. They send out a block to be mined, and get updates from a miner whenever a miner gets a partial solution. The shifts in the value of Bitcoin can be huge, too: Normal people use software [1] that hides what is really going on, but I wanted to get a hands-on understanding of the Bitcoin protocol. Excellent work. Retrieved 10 October
To make it what is the cheapest way to buy cryptocurrency what does the bible say about cryptocurrency to enter a recipient's address, many wallets can obtain the address by scanning a QR code or touching two phones together with NFC technology. A government that chooses to ban Bitcoin would prevent domestic businesses and buy bitcoins online with credit card no verification ethereum parity browser from developing, shifting innovation to other countries. The list of peers changes every few seconds, whenever someone runs a client. Economics, Technology, and Governance". Behind the scenes, the Bitcoin network is sharing a public ledger called the "block chain". Assuming I have the entire block chain on my laptop. Conde Nast. Retrieved 2 September I could also verify the success of this transaction by looking in my Bitcoin wallet and by checking online. Is Bitcoin anonymous? Since transactions can have multiple outputs, users can send bitcoins to multiple recipients in one transaction. Archived from the original on 20 October Note that the. Thank you. A network of communicating nodes running bitcoin software maintains the blockchain. Hidden categories: Archived from the original on 27 May Cryptography Bitcoin uses digital signatures to ensure that only the owner of bitcoins can spend .
Digiconomy estimates that the entire Visa credit network uses about a three-thousandth the total energy of Bitcoin. International Business Times. In addition, anyone can process transactions using the computing power of specialized hardware and earn a reward in bitcoins for this service. How does the network agree on which blocks are valid? And it is. To be accepted by the rest of the network, a new block must contain a proof-of-work PoW. Retrieved 11 August View Comments. Bitcoin, along with other cryptocurrencies , has been identified as an economic bubble by at least eight Nobel Memorial Prize in Economic Sciences laureates, including Robert Shiller , [] Joseph Stiglitz , [] and Richard Thaler. Mining is also the mechanism for new bitcoins to enter the system. According to researchers, other parts of the ecosystem are also "controlled by a small set of entities", notably the maintenance of the client software, online wallets and simplified payment verification SPV clients. While this is an ideal, the economics of mining are such that miners individually strive toward it. Is Bitcoin useful for illegal activities? It's just a matter of packing the data into binary.
This protects merchants from losses withdraw tokens from etherdelta to metamask bittrex omg coin by fraud or fraudulent chargebacks, and there is no need for PCI compliance. Principles, Trends, Opportunities, and Risks". Normal people use software [1] that hides what is really going on, but I wanted to get a hands-on understanding of the Bitcoin protocol. I try to write it on VB. San Francisco Chronicle. It is always important to be wary of anything that sounds too good to be true or disobeys basic economic rules. Given the importance that this update would have, it can be safely expected that it would be highly reviewed by developers and adopted by all Bitcoin users. Most of the time the hash isn't successful, so you modify the block slightly and try again, over and over billions of times. IO Steem. Let's say we have computers and would like to. A Bitcoin transaction has, broadly speaking, the same three components. XX BNF: Creating a bitcoin address requires nothing more than picking a random valid private key and computing the corresponding bitcoin address. Archived from the original on 7 February Retrieved 10 October A confirmation means that there is a consensus on the network that the bitcoins you received haven't been sent to anyone else and are considered your property.
The Bitcoin network has no built-in protection mechanisms when it comes to accidental loss or theft. LSE Research Online. I started by bying bitcoins from Coinbase and putting 0. Has the problem of conflicting transactions has just been replaced by the problem of conflicting blocks? Retrieved 26 July Those users can then spend their new Bitcoins on goods and services, and the process repeats. The idea is to start with all the transaction hashes. Yahoo Finance! Bitcoin miners are processing transactions and securing the network using specialized hardware and are collecting new bitcoins in exchange. Nakamoto is estimated to have mined one million bitcoins [28] before disappearing in , when he handed the network alert key and control of the code repository over to Gavin Andresen. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. Legality of bitcoin by country or territory.
Network nodes can validate transactions, add them to their copy of the ledger, and then broadcast these ledger additions to other nodes. TheVerge News. Senate held a hearing on virtual currencies in November Archived PDF from the original on 16 June First, B's public japan bitcoin legal tender coinbase do not send eth mining rewards must correspond to B's address in the previous transaction, proving the public key is valid. Archived from the original on 10 December Really interesting stuff about the alto and the ibm mainframes and stuff. Satoshi Nakamoto could be an individual man or woman, an internet handle, or a group of people, but nobody actually knows. On 24 October another hard fork, Bitcoin Goldwas created. E64G Ephifany core card and use computing paralell and I not have idea How begin? Forbes named bitcoin the best investment of Transactions can be processed without fees, but trying to send free transactions can require waiting days or weeks.
Transactions can be processed without fees, but trying to send free transactions can require waiting days or weeks. And right now, bitcoin protocol research is taking all my time. In addition, the miner gets any fees associated with the transactions in the block. The peer-to-peer Bitcoin system verifies the transaction via the global network, transferring the value from one user to the next and inserting cryptographic checks and verification at many levels. Mining What is Bitcoin mining? But come on. A network of communicating nodes running bitcoin software maintains the blockchain. Thus, cryptographic hashing becomes a good way to implement the Bitcoin "proof-of-work". Retrieved 20 December Receiving notification of a payment is almost instant with Bitcoin. Multiplying my PC's performance by the current difficulty shows it would take my PC about 35, years to mine a block. Bitcoin Core. Can bitcoins become worthless? Is the above double hash used to sign each input no matter who the owner , or are different hashes signed? The hash problems get exponentially harder, and every four years the size of the reward cuts in half. If they successfully mine a block, why not submit it themselves so they can claim the full mining reward, rather than splitting it? Retrieved 29 December
How Are Bitcoins Spent?
You can trade Bitcoins directly to another person for cash, though this is much more dangerous than going through an established system. I'm having a hard time grasping the "degrees of freedom" available to the miner. Any of these changes will result in totally different hashes, so the nonce values can be tried again. A hardware wallet peripheral which processes bitcoin payments without exposing any credentials to the computer. The long-term viability of Bitcoin as a medium for wealth has yet to be determined. The script sends a version message, receives and ignores the peer's version and verack messages, and then sends the transaction as a tx message. Bitcoins are blocks of ultra-secure data that are treated like money. CS1 maint: Users who rely on a bitcoin trading exchange such as Bitfinex, Binance or Kraken to exchange currency for bitcoin have to divulge their personal information to that exchange to create an account. LSE Research Online. Archived from the original on 10 July The difficulty and competitiveness of mining is a key part of Bitcoin security, since it ensures that nobody can flood the system with bad blocks. Great article and given that you're still answering questions 3 years later I thought I'd repeat an unanswered question from earlier that piqued my curiosity. What bitcoin protocol message goes out on the wire when a miner successfully solves a block and releases it into the wild? Because of bitcoin's decentralized nature and its trading on online exchanges located in many countries, regulation of bitcoin has been difficult. The bitcoin blockchain will only show that a transaction has taken place between two public keys an identifier of 34 random alphanumeric characters , indicating the time and amount of the transaction. True, but it also has the something-for-nothing vibe that makes physicists nuts. The number of new bitcoins created each year is automatically halved over time until bitcoin issuance halts completely with a total of 21 million bitcoins in existence. Archived from the original on 5 January Several studies have also shown that it is possible to use network analysis and other methods to observe and potentially tie back blockchain transactions to certain websites and individuals.
Because i already have 1. Thus, after a lot of effort, I had successfully created a transaction manually and had it accepted by the. So yes you do hash the odd transaction at the end to. That last bit is where the freak-out comes in. Much appreciated. Archived from the original on 3 October Bitcoins are created crypto calendar cryptocurrency index etf a decreasing and predictable rate. First, B's public key must correspond to B's address in the previous transaction, proving the public key is valid. Bitcoin's most common vulnerability is in user error.
The purpose of mining
Since transactions can have multiple outputs, users can send bitcoins to multiple recipients in one transaction. This is a fairly standard transfer for most of the verified markets and exchanges. Thank you in advance. Can bitcoins become worthless? Ars Technica. For more information on finding Bitcoin peers, see How Bitcoin clients find each other or Satoshi client node discovery. A miner can then run through all the nonce and extranonce2 values without duplicating work. In other words, instead of making mining computationally expensive, you just make it expensive. The first regulated bitcoin fund was established in Jersey in July and approved by the Jersey Financial Services Commission. Currently, the miners on the Bitcoin network are doing about 25 million gigahashes per second. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. Retrieved 16 January View Comments. Archived PDF from the original on 22 September Degree of acceptance - Many people are still unaware of Bitcoin. Once checked, the new transactions are added as a new block to the blockchain. Distributed Right-Wing Extremism.
The vast number of valid private keys black ethereum bitcoin rapid price increase it unfeasible that brute force could be used to compromise a private key. I'd be interested in just how a proxy would 'split' the work, to ensure each of the computers wasn't duplicating work. Bitcoin and Other Virtual Currency-related Investments". Railslove GmbH Anschrift wie oben. Retrieved 9 June That fall in demand will in turn cause merchants to lower their prices to try and stimulate demand, making the problem worse and leading to an economic depression. Using the raw Bitcoin protocol. This is very similar to investing in an early startup that can either gain value through its usefulness and popularity, waves coffee house bitcoin gavid andresen bitcoin just never break. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. This public key is used to verify the signature on a transaction. European Banking Authority. Transaction fees are used as a protection against users sending transactions to overload the network and as a way to pay miners for their work helping to secure the network. Archived from the original on 3 April What am I missing?

I waiting for. However, these features already exist with cash and wire transfer, which are widely used and well-established. Retrieved 10 January The Daily Dot. Apparently how to use bitcoin core to open corrupted wallet 2gb gpu zcash big-ending and little-endian isn't confusing enough so this hash value also has every block of 4 bytes reversed. Bitcoin miners perform this work because they can earn transaction fees paid by users for faster transaction processing, and newly created bitcoins issued into existence according to a fixed formula. Because Bitcoin is a distributed peer-to-peer system, there is no central database that keeps track of who owns bitcoins. Anybody can become a Bitcoin miner by running software with specialized hardware. For broader coverage of this topic, see Cryptocurrency wallet. For example, if bitcoin transfer fee coinbase satoshi nakamoto original source code forget the change address in a transaction, excess bitcoins will go to the miners as a fee. Using the raw Bitcoin protocol.
By using this site, you agree to the Terms of Use and Privacy Policy. The code is still valid, although I'm not actively maintaining it. A transaction uploaded to Bitcoin, as seen in Wireshark. Fourth, bitcoin mixing algorithms, such as CoinJoin, link users and allow them to pay together such that the bitcoins are mixed. Awesome article. This script only includes the public key hash the address and requires the redeemer to provide the public key. Reasons for changes in sentiment may include a loss of confidence in Bitcoin, a large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. I find it very confusing though, since it doesn't distinguish between the address and the public key. Some countries are investigating bitcoin as a growing commodity market, some take the same stance as the US declaring them assets, and some have explicitly banned their use for transfer of goods or services though the means of enforcing those bans are limited. Needless to say, my first few transaction attempts weren't successful - my faulty transactions vanished into the network, never to be seen again. This ledger contains every transaction ever processed, allowing a user's computer to verify the validity of each transaction. Photo credit: Over the course of the last few years, such security features have quickly developed, such as wallet encryption, offline wallets, hardware wallets, and multi-signature transactions. Retrieved 10 October Archived from the original on 18 September Retrieved 26 March That evolved.
Retrieved 15 May Notes and references [1] The original Bitcoin client is Bitcoin-qt. Replaying blocks bitcoin core transaction codes for bitcoin you are mining with multiple devices or you buying bitcoin over 2000 digix ethereum a pool administrator, you have to divide the work to avoid calculating the same hash twice make sure they never use the same c. This is ethereum address to qr code books on trading bitcoin called "mining". Lack of adoption and loads of volatility mean that cryptocurrencies satisfy none of those criteria. If an address received bitcoins in a transaction and you just want to spend 1 bitcoin, the transaction must spend all Unlike bitcoin, these competitors accept and dispense cash and do not require the use of the Internet which is a distinct advantage in lower income countries. Retrieved 2 July Retrieved 26 March Retrieved 9 March Will point readers here when they ask how mining results in BTC. To be accepted by the rest of the network, a new block must contain a proof-of-work PoW. Archived from the original on 2 November Yahoo Finance. The Bank for International Settlements summarized several criticisms of bitcoin in Chapter V of their annual report.
Since inception, every aspect of the Bitcoin network has been in a continuous process of maturation, optimization, and specialization, and it should be expected to remain that way for some years to come. The private key is simply a random bit number. The Daily Dot. Any Bitcoin client that doesn't comply with the same rules cannot enforce their own rules on other users. Right now, bitcoin looks increasingly like a tool for speculation rather than a viable, mainstream currency. This is also a key part of Bitcoin security, since it ensures that transactions cannot be changed once they are part of a block. I have a question regarding competition between the pools. Archived from the original on 14 January We saw bitcoin as a great idea, as a way to separate money from the state. This makes bitcoin pseudonymous. If you run a Bitcoin client, you become part of that network.
All pool will try to put the next node, but the pool with less power will have to start the job because the previous block was change. Thank you for a great explanation. However, you should be aware that any conventional earnings you receive from dealing in Bitcoin will be treated in the usual way. This allows the core of Bitcoin to be trusted for being completely neutral, transparent and predictable. From Wikipedia, the free encyclopedia. These companies use analytics on the bitcoin blockchain to link bitcoin addresses to web entities and help their customers assess the risk of illegal activities. I'm using version somewhat arbitrarily. In general, it is common for important breakthroughs to be perceived as being controversial before their benefits are well understood. However, these features already exist with cash and wire transfer, which are widely used and well-established. I try to write it on VB. Someone with a slow PC could get lucky and mine a block or even someone mining on an old punchcard computer. Bitcoin software Alternative currencies Application layer protocols Computer-related introductions in Cryptocurrencies Currencies introduced in Digital currencies. What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force.

 Fr
Fr 中文
中文