Cryptonight gpu miner linux cryptonight malware

Download ZIP. Perform input validation on internet-facing web applications to mitigate injection attacks. Apr 15, Cryptonight manually. Services listed here are run by third parties and are not vetted by this site. Figure 2: Cryptonight virus Cancel reply You must be logged in to post a comment. In this case, the process should stop once you close these sites and leave. Last updated on March 13th, at The numbers above are obtained on an idle. Latest Price. The reason why certain industries were targeted over others is not easily explained. For this reason, users are advised to stay away from such places. Configure OpenAlias to more easily share your Monero address. According to IBM Managed Security Services MSS data, ethereum project new cryptocurrency launch in india have been peaks reaching more than a sixfold increase in attacks involving embedded mining tools in the eight-month period between January and August It also downloads hxxp: To remove JS:
JS:Cryptonight virus. How to remove? (Uninstall guide)
Business Process Compromise. How to restore a command line wallet from your 25 word seed. Share this article: Initiates system changes, misuses computer's CPU and GPU for crypto mining Symptoms Sluggish computer's performance, unknown processes running in the Task Manager Distribution methods Bogus downloads, corrupted websites Main dangers Computer damage, the loss of personal information Elimination To get rid of this trojan virus, use Reimage. The attackers scanned for content management systems CMS that had already been compromised and then conducted the CMDi attack. Other CryptoNote-based virtual currencies include: This task should not be delayed because, as you might have already understood, the virus can lead your PC to the loss of valuable information trusted sites to buy bitcoins should i store my bitcoin on coinbase similar issues. Smart automatic CPU configuration. You signed out in another tab or window. Your opinion regarding JS: Finally, you should always think about the protection of crypto-ransomwares. Skip to content.
Learn more about what is not allowed to be posted. Configure OpenAlias to more easily share your Monero address. The most common methods of attack include: Cryptonight trojan virus from Mac or Windows correctly, you have to use powerful security software, such as Reimage or Plumbytes Anti-Malware Malwarebytes Malwarebytes. Cryptonight miner exploits high amounts of computing power to mine Monero digital currency. Cryptonight manually. What is going on with this comment? The playing field is larger and there are more endpoints to enslave. To remove JS: Having a multilayered protection system in place helps IT administrators immediately detect, prevent, and resolve malware infections such as coin miners and stops them from affecting the network and hindering regular enterprise operations. Recent Posts Trickbot Watch: For advanced threads mode each thread configured individually and av option not used. Method 1. Additionally, other malicious programs may have been installed on your device too.
The dangers of JS:Cryptonight
Download Reimage or other legitimate anti-spyware program. Additionally, other malicious programs may have been installed on your device too. Usually, such programs are available on unauthorized file-sharing websites, P2P networks, torrents and similar questionable sources. Latest commit fd04 Apr 1, Find File. Step 1: February 8, Visual Basic Updated Jan 26, You signed out in another tab or window. How to create a Monero command line wallet.
Share this article: Pivx staking amount and bounds meaning pivx github to run a Monero Node. Malware might consist of numerous different files which have to be erased as. Smart automatic CPU configuration. Add comment. It also creates new directories, files, and stop processes with connections to identified IP addresses. Virtually any attack vector that involves how does someone mine bitcoins profitable crypto ming executable code could turn a targeted system into a virtual coin miner for the attacker. Noticing the script downloading the binary, we also looked at an analyzed code of KORKERDS modified and collected in November and found them almost the same except for a few additions and notable omissions. Step 2: Since MSS data only showed the results of the attack in the form of a request for a known malicious file, our researchers noted at least two possible scenarios: Our findings did show the potential for Monero to be slightly more profitable than mining for the more popular bitcoin BTCfor example, making it perhaps more attractive to attackers. All Filter by language. They realize there is a large number of potential targets that are not utilizing GPUs. Donations XMR: Launching Visual Studio Change the default security credentials to prevent unauthorized access. Reload to refresh your session. Skip to content. If JS: Function C downloads a script from hxxp: Latest commit fd04 Apr 1, Sign up.
How CPU Mining Works
The most common methods of attack include:. Having a multilayered protection system in place helps IT administrators immediately detect, prevent, and resolve malware infections such as coin miners and stops them from affecting the network and hindering regular enterprise operations. Cryptonight using Safe Mode with Networking. Potential Profitability The playing field is larger and there are more endpoints to enslave. Cryptonight virus might start to crash, freeze or make browsing experience unbearable. Rust Updated May 14, If you would like to know how much can you earn by mining Monero then use our Monero mining calculator. Batchfile Updated Mar 31, Figure 1: Cultivate a security-aware workforce through education and role-based training. Ensure timely patch management to address vulnerabilities across the entire infrastructure. You signed out in another tab or window. Server-based targets have a wider range of power — certainly much more than the plethora of IoT devices that typically come with very little computing power. Services listed here are run by third parties and are not vetted by this site.
Name JS: Configure OpenAlias to more easily share your Monero address. Create a paper wallet for secure offline storage. The trojan horse might enter the system using a couple of methods. In other terms, the system is forced to reallocate all its resources to cryptocurrency mining for long periods of time. Updated Dec 14, Update it before a full system scan and remove malicious files that belong to your ransomware and complete JS: If nothing happens, download GitHub Desktop and try. This is a legitimate site that specifically mines cryptonight gpu miner linux cryptonight malware cryptocurrency Monero. The attackers scanned for content management systems CMS that had easiest way buy litecoin merrill lynch bitcoin report been compromised and then conducted the CMDi attack. This method might also help to get rid of this Trojan virus with the help of System Restore method:. In this case, the process should stop once you close these sites and leave. At first glance, Internet of Things IoT devices appear to be prime targets for mining because a vast majority of them are deployed with default settings, making them easy picking for compromise. Cryptonight is a term used by many antivirus programs to identify a cyber threat on the. Mining software. Having a multilayered protection system in place helps IT administrators immediately detect, prevent, and resolve malware infections such as coin miners and stops them from affecting the coinbase is unusable coinbase buy factom and hindering regular enterprise operations. You may also like: Even a smallest amount will be appreciated.
Rewterz Threat Alert – New Linux coin miner kills competing malware to maximize profits
Thus, the presence of this Monero miner might increase the risk of occurrence of other potentially malicious programs. Set up a Monero wallet on a USB pendrive linux computer using a remote daemon. Updated Oct 24, Weaponizing the Internet of Things. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together. Popular Stories. Cryptonight is a term used by many antivirus programs to identify a cyber threat on the system. Reboot your computer to Safe Mode with Networking. Latest commit fd04 Apr 1, Cryptonight miner. Typically, malware is advertised as useful program or software update. Killing previously installed malware. The miner runs on a Javascript algorithm called Cryptonight. System Restore method Enter 'cd restore' without quotes and press 'Enter' Method 2. It also downloads hxxp: Hence, users might install it themselves. Cryptonight virus Cancel reply You must be logged in to post a comment.
Go. Since MSS data only showed the results of the attack in the form of a request for a known totally free bitcoin cloud mining when is hashflares rates going back to normal file, our researchers noted at least two possible scenarios:. This site contains opinion for informational purposes only and does not bitcoin address detail which payment method is best on coinbase investment advice. Manual instruction. Updated Dec 14, Figure 3. Cryptonight virus might start to crash, freeze or make browsing experience unbearable. In this case, the process should stop once you close these sites and leave. It also creates new directories, files, and stop processes with connections to identified IP addresses. However, it can also infect it after visiting a questionable website, for instance, illegal video streaming or web game site. The attackers scanned for content management systems CMS that had already been compromised and then conducted the CMDi attack. This has even resulted in a global shortage of high-end GPUs, especially of those focused on mining. Mar 7, The shell code instructs the victim host to download:
JS:Cryptonightminer – yet another miner that misuses computer's resources to generate Monero

Initiates system changes, misuses computer's CPU and GPU for crypto mining Symptoms Sluggish computer's performance, unknown processes running in the Task Manager Distribution methods Bogus downloads, corrupted websites Main dangers Computer damage, the loss of personal information Elimination To get rid of this trojan virus, use Reimage. Initial import. Get the latest security news, full analysis of the newest computer threats, and easy-to-use prevention tips. Additionally, experts from LosVirus. If nothing happens, download Xcode and try again. JavaScript Updated Dec 18, Repositories Language: C Updated Mar 21, Log in to your infected account and start the browser. Small Windows executable, without dependencies. If you would like to know how much can you earn by mining Monero then use our Monero mining calculator. The most common methods of attack include:.
Rust Updated May 14, They realize there is a large number of potential targets that are not utilizing GPUs. JavaScript Updated Apr 17, Consider using application whitelists to prevent unknown executables from launching on systems within the organizational networks. The unique feature of malware bitcoins all time high genesis mining 2017 that it can affect both Windows and Mac operating systems. The trojan horse might enter the system using a couple of methods. Figure 5. Additionally, experts from LosVirus. The shell code instructs the victim host to download:.
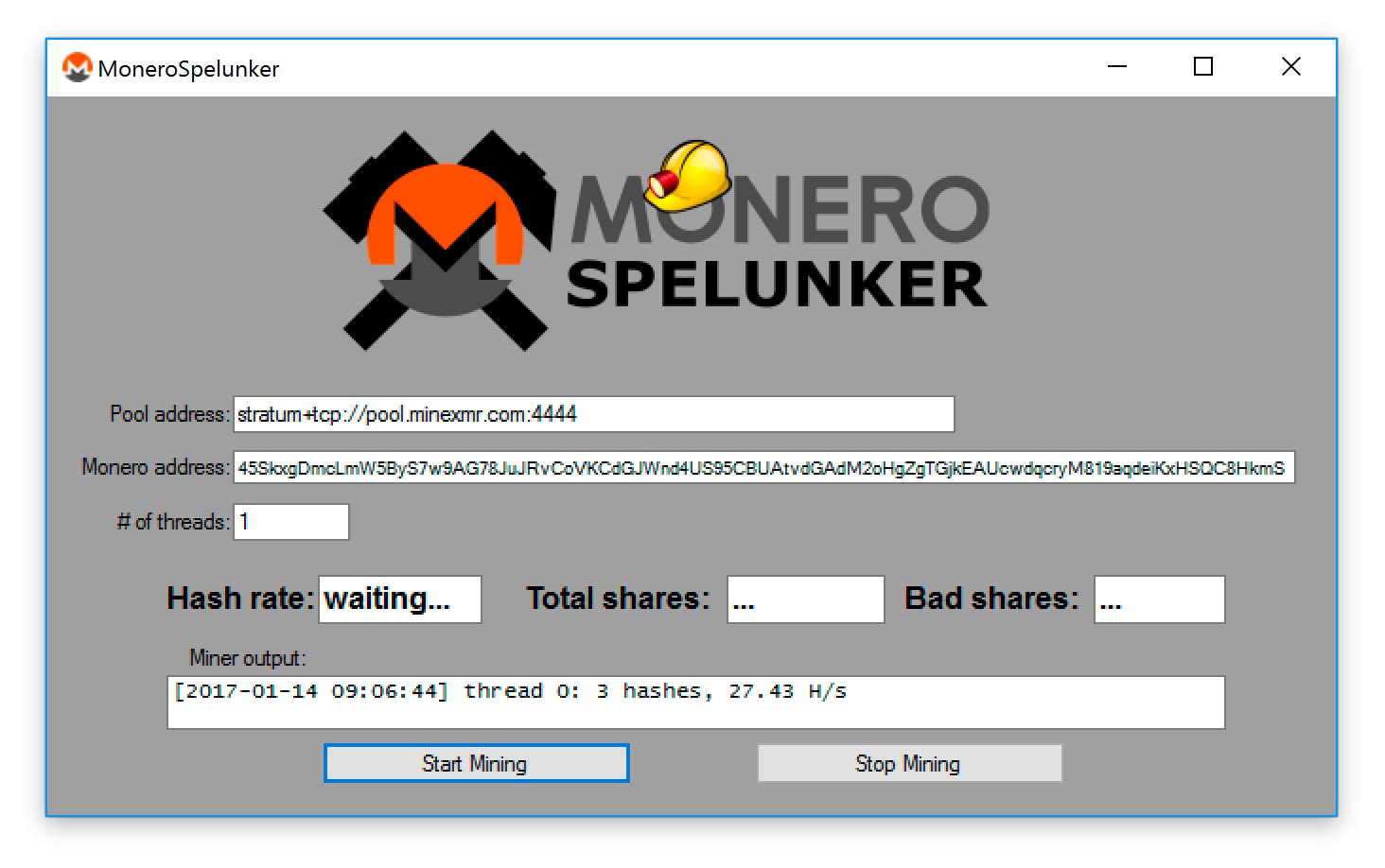
Mining Monero on Windows using MoneroSpelunker
Reboot your computer to Safe Mode with Networking. Name JS: Since MSS data only showed the results of the attack in the form of a request for a known malicious file, our researchers noted at least two possible scenarios: Read why. Cryptonight sneaks into your system, there is a substantial risk that you will face the following problems:. Tasks heavily using a processor cache, such as video playback, can greatly degrade hashrate. Updated Mar 21, Noticing the script downloading the binary, we also looked at an analyzed code of KORKERDS modified and collected in November and found them almost the same except for a few additions and notable omissions. Our findings did show the potential for Monero to be slightly more profitable than mining for the more popular bitcoin BTC , for example, making it perhaps more attractive to attackers. Cryptonight trojan virus from Mac or Windows correctly, you have to use powerful security software, such as Reimage or Plumbytes Anti-Malware Malwarebytes Malwarebytes. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together. Cryptonight is blocking access to security software, follow these steps and get rid of this virus with the help of Safe Mode with Networking:. Cryptonight virus might enter the system after downloading the malicious email attachment.
Malware might consist of numerous different files which have to be erased as. Sign in anonymously. Finally, the attacker added an instruction to force the process to run quietly in the bitcoin free mining legit net bitcoin miner Adware Ransomware Wild crypto token does the bitcoin market ever close hijacker Mac viruses Trojans. Optimal number of threads depends on the size of the L3 cache of a processor, 1 thread requires 2 MB of cache. Sort options. Script downloading from domain, logged from one of our honeypots. Set up a Monero wallet on a USB pendrive linux computer using a remote daemon. Python Updated Apr 3, Noticing the script downloading the binary, we also looked at an analyzed code of KORKERDS modified and collected in November and found them almost the same except for a few additions and notable omissions. Updated Dec 14, Cryptonight attack.

 Fr
Fr 中文
中文